Understanding Authentication in ArcGIS Enterprise: A Guide for GIS Professionals
February 3, 2025 2025-02-05 7:23Understanding Authentication in ArcGIS Enterprise: A Guide for GIS Professionals
Understanding Authentication in ArcGIS Enterprise: A Guide for GIS Professionals
ArcGIS Enterprise is much more than a GIS and mapping platform, it’s a full-fledged enterprise IT solution. This means that, beyond GIS principles, it’s also built on core IT concepts, making security and authentication crucial components of its functionality.
My Journey with Authentication in ArcGIS Enterprise
When I started at Esri nearly nine years ago, I came in with a computer science background and only a high-level understanding of GIS. Working in Technical Support, I quickly picked up GIS concepts, but I noticed something interesting—many ArcGIS Enterprise users came from GIS backgrounds and often weren’t familiar with IT-related topics, particularly authentication.
Authentication is a topic that came up repeatedly in support calls, so I want to break it down in a way that makes sense whether you have a GIS background or an IT background. In this post, I’ll walk through different authentication types, help you determine what’s best for your organization, and explain how tokens work within ArcGIS Enterprise.
What is Authentication?
Authentication is a security process that verifies the identity of a user or application attempting to access a system. Once authentication confirms the identity, authorization determines what resources—such as maps, data, or apps—the user is allowed to access.
A well-configured authentication system can streamline access by enabling single sign-on (SSO), meaning users don’t have to manage separate credentials for different applications. Instead, one central authentication system allows users to log in once and access multiple systems seamlessly.
ArcGIS Enterprise offers multiple authentication methods, each with unique benefits. Choosing the right one enhances security, simplifies user management, and improves the overall user experience.
Why Authentication Matters
In today’s digital world, securing GIS data and web services is more important than ever. Proper authentication helps protect sensitive information and maintain trust within an organization.
A simple analogy: think of authentication like checking into a hotel. At the front desk, you present an ID (like a driver’s license or passport) to confirm your identity. Once verified, you receive a key that grants access only to your room. Similarly, authentication in ArcGIS Enterprise ensures that users can only access the parts of the system they’re authorized for.
As data security becomes increasingly critical, understanding who has access and how is essential for maintaining control and compliance.
What is an Identity Store?
An identity store is a system that manages user accounts and authentication credentials. It defines how authentication happens and how user group memberships are managed.
There are two primary types of identity stores:
- Built-in Identity Store – Manages user credentials directly within ArcGIS Enterprise.
- Organization-Specific Identity Store – Integrates with an organization’s existing authentication system.
ArcGIS Enterprise supports integration with various identity providers (IdPs), including:
- SAML (Security Assertion Markup Language)
- OIDC (OpenID Connect)
- LDAP (Lightweight Directory Access Protocol)
- IWA (Integrated Windows Authentication)
Each of these identity store options requires specific configurations to enable secure authentication and authorization.
Overview of Authentication Types
ArcGIS Enterprise provides flexibility in authentication, allowing organizations to choose the best fit for their security and user management needs. Using the hotel analogy, your hotel key could be a physical key, a keycard, or even a digital key on your phone. Similarly, authentication methods in ArcGIS Enterprise vary based on the organization’s requirements.
Authentication Methods in ArcGIS Enterprise
- Built-in Identity Store
- The default method where user accounts are created directly within ArcGIS Enterprise.
- Stores usernames, passwords, roles, and group memberships internally.
- Ideal for initial setup, development, and testing environments.
- Organization-Specific Identity Store
- Allows users to log in with existing corporate credentials.
- Improves security by integrating with Identity Providers (IdPs) such as Active Directory.
- Reduces the need for users to manage multiple credentials.
- Web-Tier Authentication (IWA)
- Authentication is handled at the web server level before users reach ArcGIS Enterprise.
- Example: Integrated Windows Authentication (IWA) automatically signs users in using Windows credentials.
- Portal-Tier Authentication (LDAP)
- Uses an organization’s Active Directory or LDAP identity store for authentication.
- Can be configured without relying on SAML.
- SAML Authentication
- A widely used open standard that allows single sign-on (SSO) across multiple systems.
- ArcGIS Enterprise acts as a Service Provider (SP), while an organization’s IdP (such as Okta or Microsoft Entra ID) handles authentication.
- OIDC (OpenID Connect)
- Another open standard supported by various identity providers.
- ArcGIS Enterprise can integrate with IdPs like Okta and Google for authentication.
If both ArcGIS Online and ArcGIS Enterprise use the same SAML or OIDC identity provider, users can experience single sign-on (SSO) across both platforms. However, they remain separate systems, meaning user permissions, groups, and content are not automatically shared.
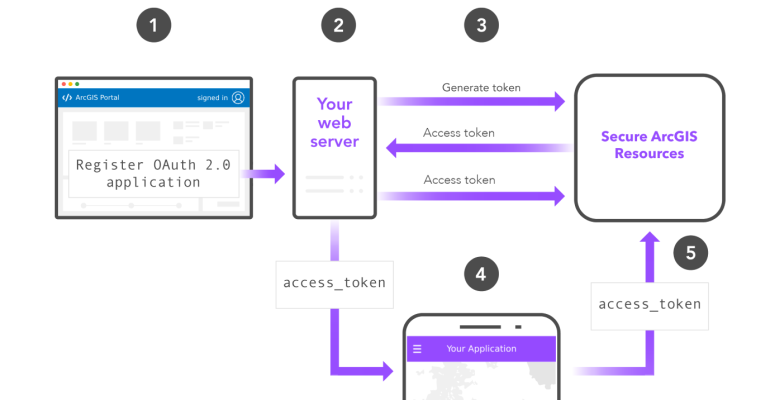
How Tokens Work in ArcGIS Enterprise
Tokens play a key role in authentication, ensuring secure access without requiring users to constantly re-enter credentials. Here’s how token-based authentication works:
- User Logs In – The user enters their credentials (e.g., username and password).
- Token Issued – The authentication server generates a unique token.
- Token Used for Access – The user includes this token in subsequent requests.
- Token Expiry – Tokens have a limited lifespan. Once expired, the user must log in again.
Token-based authentication enhances security while providing a seamless user experience.
Growing Security Needs
With increasing cybersecurity threats, organizations are moving beyond password-based authentication. Many are implementing multi-factor authentication (MFA), which requires an additional verification step, such as a mobile authentication code, to enhance security.
Using a centralized identity provider allows organizations to:
- Enforce MFA policies for added protection.
- Simplify user management by applying the same authentication rules across multiple systems.
- Provide seamless access to both ArcGIS Online and ArcGIS Enterprise.
Choosing the Right Authentication Method
Selecting the right authentication approach depends on:
- Security and compliance requirements
- Ease of user access and management
- Integration with existing IT systems
SAML and OIDC are among the most commonly used authentication methods because they support single sign-on (SSO) and integrate well with enterprise identity management systems.
By aligning authentication methods with broader IT strategies, organizations can ensure secure, efficient, and user-friendly access to ArcGIS Enterprise.
For more in-depth guidance, visit the ArcGIS Architecture Center.